How Secure Is Your Crypto Business?
Does your business accept crypto payments? Check if you’re using cryptocurrency security best practices with these 7 risk assessment questions.

Accepting cryptocurrency payments brings many benefits to freelancers and businesses. Think near-instant payments anywhere in the world, no customer chargebacks, and access to a huge emerging market.
As it’s still a relatively new industry lots of early adopters aren’t aware of the best practices. We’re going to look at 7 cryptocurrency security risks your business needs to consider. We’ll also discuss the best way to protect yourself from each.
Cryptocurrency security risks
Many of the risks we’re going to look at will be familiar to tech-savvy individuals. It’s often old technology applied in novel ways – taking advantage of the unfamiliarity of the crypto world.
Do you copy-and-paste blockchain addresses?
This is one of the easiest risks to succumb to. There’s malware that can hijack your clipboard. You copy the address you want to pay and when you paste the address it’ll be automatically replaced with a different one.
You’ve just unknowingly sent a payment to a malicious actor and because the blockchain is decentralized, you’ve no way of retrieving the money. If you need to copy-paste an address, always visually check it’s correct.
Do you use a VPN (Virtual Proxy Network)?
If you do any of your business on a shared or public WiFi network, then anything you do is technically at risk. Hackers love public WiFi because it’s so much less secure. If you’re sending sensitive data on a public network you should use a VPN.
It’ll give you the added layer of security required to prevent the hacker from being able to access your private data. Ensure you’re using a trusted VPN provider. A report by CSIROscope found that over 80% of free Android VPNs request access to sensitive device data.
Do you use a password manager?
Do you keep your cryptocurrency stored on an exchange? Experts strongly recommend that you use a password manager to keep your online accounts safe with a strong and unique password for each of them.
However, bear in mind that studies have also shown that centralized exchanges are hacked because someone gained access to their online password manager.
Therefore, we’d advise enabling 2-factor authentication (2FA) for your online accounts. This means that in addition to your password, you’ll need a code generated by one of your devices before you can sign in. It's also recommended to have 2FA enabled for your password manager to prevent hackers from using passwords for online accounts that don't have the 2FA feature. This is much safer. In fact, according to a statement by Microsoft, 99.9% of automated attacks will be blocked when 2FA is enabled.
Do you regularly run virus scans?
There are a lot of viruses and malware emerging that specifically target cryptocurrency wallet information – ElectroRAT for example. Hackers know there’s a lot of money in the industry and that many people aren’t up-to-date on cryptocurrency security best practices. It’s an appealing target for them.
We’ve already discussed a few specific ways they can access this data. How to mitigate the risk? Scan all downloaded files and regularly run a complete virus scan of your entire system. In addition, ensure your antivirus program is regularly updated to the latest version.
Can you spot a phishing email?
Most people would recognize an email from a money-seeking Nigerian prince as a scam. Unfortunately, the phishing attacks of today are much more sophisticated. They can look like they’ve been sent from a crypto exchange – with a somewhat relevant email address.
Another common one is advertising new digital products with a giveaway as an incentive – this happened with Celsius wallet recently. Avoiding these is as simple as verifying the authenticity of any emails you receive. The easiest way to do this is to navigate to the main site and log in directly.
Do you use third-party crypto services?
The industry is growing exceptionally fast. New projects and services are launched almost daily. Maybe you’re using a payment processor or a wallet management system?
The issue with some of these services is that they haven’t prioritized security. Although the blockchain is very secure, the weak links are the endpoints where users directly interact with the blockchain. As there are minimal cryptocurrency security requirements for third-party apps it can become a vulnerability.
An Accenture blockchain security report says, “The most direct and potentially easiest method of attacking any technology solution is through the endpoint vulnerabilities.”
If you’re going to give control to a third party you need to ensure that they take security seriously. This includes being able to explain how they use encryption and regularly issues updates – legacy software is a prime target for hackers.
Where do you store your cryptocurrency?
There’s not a right answer to this question. It depends on your business needs. Storing your crypto in a wallet that’s connected to the internet – known as a hot wallet – is convenient but exposes you to more risk.
Storing them in a wallet isolated from the internet – known as a cold wallet– is less convenient but maximizes security. Cryptocurrency platform Roll had the details of a hot wallet exposed in a recent data breach. This resulted in a loss of about $5.7 million. This could potentially have been avoided.
We’d recommend keeping the majority of your funds in a cold wallet. Ultimately, it’s a tradeoff between convenience and risk. Learn more about the different types of crypto wallets that can be best used for your business in this article.
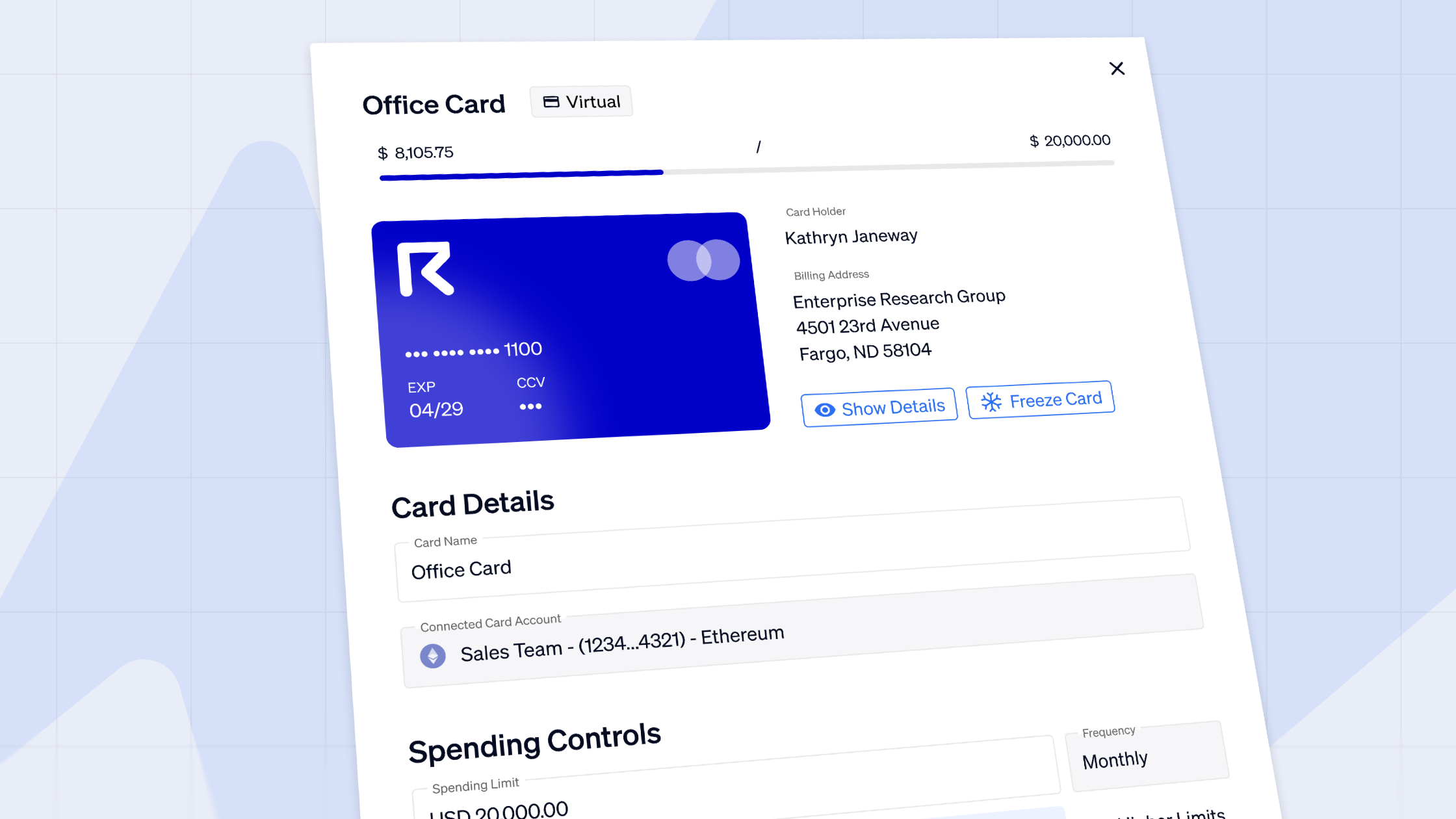
Request Finance is security you can trust
There’s a lot to be aware of if you’re sending and receiving crypto invoices manually: security risks, compliance issues, and keeping everything user-friendly. We wanted to simplify the process which is why we created Request Finance.
It’s a decentralized solution that lets you quickly send fully compliant crypto invoices. Your client can use 1-click payment, so there’s no risk of clipboard malware. Payment is verified via the blockchain which means one less opportunity for phishing emails.
We’re constantly updating our invoicing software with new features and the latest security updates. All your data remains safe and secure through the use of elliptic-curve encryption. Don’t just take our word for it. We’re trusted by some of the biggest crypto projects: 88mph, Aave, Gnosis, MakerDao, The Sandbox, and Ocean to name a few, backed by real-world use cases and testimonials about Request Finance.
Final thoughts
We’ve looked at 7 of the cryptocurrency security risks freelancers and businesses need to be aware of. Most of the risks are relatively easy to avoid if you use common sense and implement basic security measures.
If you want to make sending invoices easier and further minimize the security risks, then why not check out Request Finance? It lets you send compliant invoices in 8 seconds, gives you access to best-in-class security, and everything is packaged in a beautiful user interface.
Are you serious about security?
Ready to Supercharge Your Crypto Accounting?
Stop wasting time, manually creating journal entries. Automate your accounting now, and enjoy error-free reporting
Learn how to scale your company's crypto & fiat financial operations
Your financial complexities are our specialties. Schedule your free consultation today and discover how Request Finance can transform your financial operations
Simplify crypto and fiat financial operations today
Rely on a secure, hassle-free process to manage your crypto invoices, expenses, payroll & accounting.
Crypto finance tips straight to your inbox
We'll email you once a week with quality resources to help you manage crypto and fiat operations
Trending articles
Get up to date with the most read publications of the month.
Our latest articles
News, guides, tips and more content to help you handle your crypto finances.