PeopleDAO's Crypto Payroll Hacked for 76.5 ETH | Prevention Tips
Learn how PeopleDAO lost 76.5 ETH to a crypto payroll hack due to spreadsheet vulnerabilities. Discover how to prevent similar incidents with secure crypto payroll automation.

Many DAOs, and Web3 teams today manage their crypto payroll using Google Sheets. But this is a ticking time bomb, waiting to be exploited by hackers.
In this article, we’ll explain the dangers of using spreadsheets to manage crypto payroll, analyzing the case study of how PeopleDAO was hacked for 76.5 ETH.
We also highlight how Web3 CFOs, and DAO treasury managers can use Request Finance to secure and automate their crypto payroll processes in a non-custodial way, using multi-sig wallets like Gnosis Safe.
The dangers of using Google Sheets for crypto payroll
Many DAOs, and companies that manage their payroll in crypto rely on Google Sheets, or Excel. Spreadsheets and .csv files are also commonly used by many teams to manage airdrops, and other crypto payouts to whitelisted token sale investors, or DAO contributors.
At first glance, it seems like the natural thing to do. Google Sheets are cloud-based collaborative spreadsheets. This allows decentralized teams to collaboratively manage a contact book of DAO contributors, or employees and their crypto wallet addresses.

When the time comes to process crypto payroll payouts, or airdrops - DAO treasury managers, or finance and operations teams will copy and paste the wallet addresses from this spreadsheet, or upload a .csv file of wallet addresses into a multi-sig wallet like Gnosis Safe.
The quorum of authorized signers then approves the transaction, which triggers the payouts to the crypto wallet addresses.
But this process is incredibly vulnerable for three reasons:
Firstly, anyone with edit permission can inject malicious data into the Google Sheet, or .csv file. A hacker could simply edit the column containing the wallet addresses to insert a different wallet address. Alternatively, a hacker can simply add another row with their own wallet address to the Sheet. They could either fake the beneficiary data and hope that no one will notice, or simply hide the row.
Secondly, this injection of malicious data into a spreadsheet is also difficult to spot. Crypto wallet addresses are long hexadecimal strings that are difficult to distinguish visually. Furthermore, wallet addresses are pseudonymous, and not inherently tied to a human-readable name.
Lastly, in cases where crypto teams rely on downloaded .csv files, or offline Excel spreadsheets to manage their crypto payroll, there is the added problem of version control. This makes corrupted data even harder to spot - whether as a result of a data breach, internal fraud, or mere negligence.
Managing crypto payroll via spreadsheets is a ticking time bomb for DAO treasury managers, and Web3 CFOs, waiting to be exploited by hackers.
In fact, that’s exactly what happened to PeopleDAO in March 2023.
Ready to Supercharge Your Crypto Accounting?
Stop wasting time, manually creating journal entries. Automate your accounting now, and enjoy error-free reporting
Learn how to scale your company's crypto & fiat financial operations
Your financial complexities are our specialties. Schedule your free consultation today and discover how Request Finance can transform your financial operations
Simplify crypto and fiat financial operations today
Rely on a secure, hassle-free process to manage your crypto invoices, expenses, payroll & accounting.
How PeopleDAO lost 76.5 ETH earmarked for payroll
PeopleDAO, a group formed to buy a copy of the U.S. Constitution had their Community Treasury on Gnosis Safe, drained of 76.5 ETH ($120,000) to a hack in March 2023. The hack targeted the DAO’s monthly contributor payout form on Google Sheets.
The DAO collects monthly contributor reward information via Google Sheets, which was mistakenly shared with edit access in a public Discord channel. The hacker gained edit access to the spreadsheet via the link.

After gaining the access, the hacker inserted a 76 ETH payment to himself in the sheet. To cover his tracks, the hacker set the row to be invisible (the missing 80th row below).
Because the malicious data injected into the spreadsheet was hidden, neither the team leads, nor the DAO’s multi-sig wallet signers were able to spot the corrupted data.

The corrupted .csv file was downloaded from Google Sheets, and uploaded to their DAO’s Gnosis Safe walletvia the CSV Airdrop tool to disburse the crypto payouts.
Given the long list of wallet addresses to be paid, 6 out of 9 multisig signers did not notice the malicious transfer, signed and executed the transaction, sending 76 ETH to the hacker's address.
Look at the image below - would you have been able to spot the erroneous entry in time?

How to securely automate crypto payroll
Processing payments like crypto payroll using spreadsheets creates an attack vector that allows malicious actors to inject themselves as beneficiaries. As the PeopleDAO hack showed - this can have devastating consequences for crypto treasuries.
But with the right tools like Request Finance, DAO treasury managers and Web3 CFOs can securely automate their crypto payroll processing.
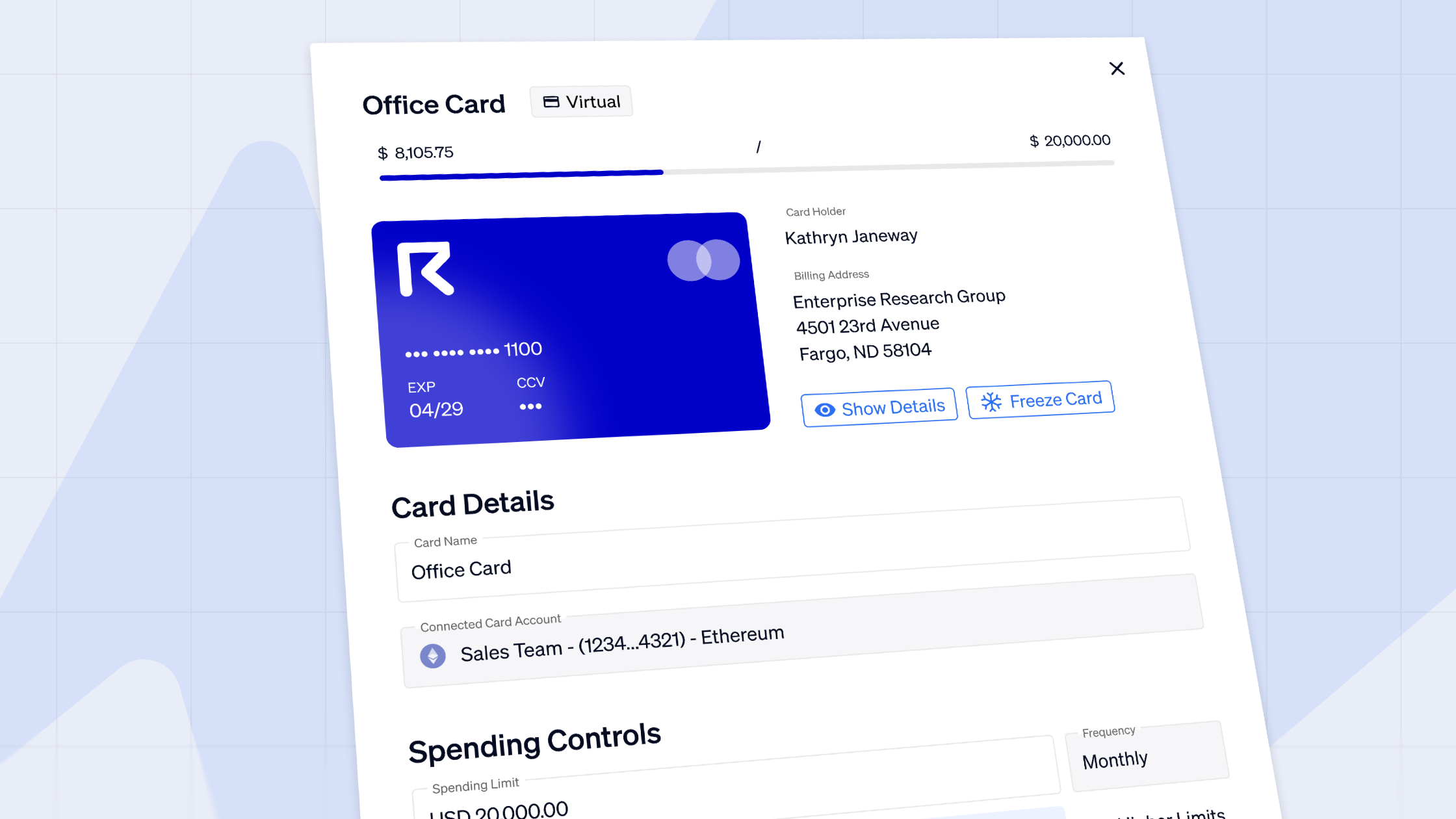
For starters, in Request Finance’s crypto payroll application, all employees’ billing information like names, roles, and wallet addresses are uploaded by an admin manager. This cannot be changed by other team members, or external parties whose roles do not grant them edit access.

Additionally, beneficiaries wallet addresses are stored in a contact database, and correlated to names, and email addresses. This makes it easy to identify duplicate entries, or non-existent team members. It would have been difficult to inject a bare wallet address, and if it were done, the anomaly would be spotted easily.

Also in the app, finance and operations teams must review and click the “approve” button for each payout claim - a crypto payroll, expense, or invoice. Only “approved” payment requests can be paid.
This enforces the practice of having teams to review each and every single claim item.

All approved payout claims are displayed in a human readable format. This makes it easy to review prior to being sent to a wallet for signing.

These are just some features in Request Finance that are designed to prevent phishing attacks that can compromise Web3 companies, and DAOs crypto payroll processes.
Concluding thoughts
When people talk about security in decentralized finance (DeFi), the spotlight is typically on more sophisticated attack vectors. These include smart contract vulnerabilities, corrupted oracles, bridges, or blockchain network security.
But sometimes the simplest attack vectors can also be equally devastating.
We’ve covered how even large companies like Amazon and Google have lost hundreds of millions of dollars to fake invoices - and how Request Finance helps prevent crypto invoice fraud.
The PeopleDAO hack highlights how the common practice of using Excel spreadsheets, or Google Sheets to manage crypto payroll is a critical vulnerability for DAOs, and companies that pay their employees, contractors, and contributors in crypto.

However, with tools like Request Finance, DAO treasury managers, and Web3 CFOs can automate their crypto payroll processes without sacrificing good governance and data security.
Crypto finance tips straight to your inbox
We'll email you once a week with quality resources to help you manage crypto and fiat operations
Trending articles
Get up to date with the most read publications of the month.
Our latest articles
News, guides, tips and more content to help you handle your crypto finances.