Best Apps for Finance Managers Managing Crypto
Discover the best crypto apps and software (accounting, asset management, payment, wallet, etc.) currently used by finance managers of companies using cryptocurrencies.

If you’re reading this, you might be a finance manager at a company that is looking to start getting into cryptocurrencies or digital assets. Now you have to figure out how to actually manage your company’s digital assets securely, and accurately documenting incoming and outgoing payments in cryptocurrency.
Manually generating and processing invoicing and accounting operations with crypto payments is not only incredibly time-consuming, but also highly prone to potentially expensive errors, and compliance failures.
Or perhaps you are the finance lead of a blockchain project that has grown so large, you actually have to start thinking about being audited. Your local accounting standards may require businesses to denominate payment records in fiat currencies. But what system do you use to determine the prices of cryptocurrencies in fiat at the point of payment, given the sharp fluctuations in cryptocurrency prices?
At Request, we’ve been working closely with CFOs at some of the most prominent companies in the crypto industry including a number of high-profile DeFi companies like Polygon, AAVE, and MakerDAO.
Here’s a list of some of the best practices, and apps currently used by finance managers of companies using cryptocurrencies.
1. Crypto wallets
2. Secure communication / messaging
3. Transaction monitoring
4. Crypto-friendly accounting software
5. Treasury management with crypto
6. Streamlining payment processing on multiple blockchains
7. Relocating
1. Choosing a crypto wallet
As a CFO in a company managing digital currencies and crypto assets, one of your first priorities is setting up a secure wallet to hold your company’s digital assets.
Wallets are like digital corporate bank accounts for your company’s cryptocurrency. More importantly, crypto wallets store the public and private keys that enable you to interact with blockchain networks.
There are two categories of wallets: hot wallets and cold wallets (sometimes called “hardware wallets”). Hot wallets are connected to the internet, while cold wallets are not.
If you regularly trade crypto on an exchange or send and receive payments in crypto, you should store some portion, or “float” of your digital currency in a hot wallet. As hot wallets are connected to the internet, you can seamlessly make crypto transactions with just a few clicks on your mobile device or computer. Whatever funds are to be held in reserve, and not actively managed, or drawn down from should be held in a cold wallet for additional security.
To find out which options were preferred by the industry, we polled CFOs among our Request Invoicing’s corporate users.
As the poll indicates, the Ledger hardware wallet, and Metamask hot wallet were among the top wallet choices used by crypto CFOs. Splitting your company’s funds between both hot and cold wallets, allow you to balance between security and ease of use.
The Gnosis Safe Multisignature wallet is ideal for companies who need to set up multiple signatures where another executive or authorized signatory in the company can co-sign for each transaction above a certain threshold. Co-signing is a critical security feature that helps prevent unauthorized access to the company’s crypto assets.
Never make the multi-signature setup public, even to internal team members. This additional layer of security is critical. It prevents malicious actors from targeting multi-signature key holders. Best practice: ensure signers are all hardware wallets.
Lukas Schor, Gnosis Safe’s product lead, explains: “Gnosis Safe is a programmable account that allows for multi-signature and other policies. This provides additional security for businesses and individuals managing crypto assets. It already stores >2.5% of the entire market cap of all crypto assets”.
To access a Gnosis Safe, the safest solution is to use a hardware wallet such as Ledger or Trezor, and connect it to a hot wallet like Metamask as a way to interact with it. Even Vitalik Buterin, the co-founder of Ethereum, uses this setup to manage the funds of his public address.
Here’s how to get started:
1. Download Metamask
2. Secure this Metamask wallet as instructed
3. Connect Metamask to a hardware wallet
4. Set up a Gnosis Safe with other authorized signatories in the company
But no single wallet, or combination of wallets is a bulletproof setup. Spread your digital assets across multiple wallet types, to hedge against the risk of either one being compromised. For instance, you can use centralized wallets across different crypto exchanges like Kraken, Coinbase, or Binance. You can also consider using multiple hardware wallets connected to a hot wallet like Metamask.
For custodial wallets, licensed custodians can also be an invaluable component of asset management. More licensed financial institutions such as commercial banks are offering custody solutions. Alternatively, you can consider crypto-native custodial service providers such as Anchorage, BitGo, and Coinbase Custody.
2. Using Secure and Private Communication Channels
Even traditional companies are targets of impersonation scams that trick employees into making bank transfers to the wrong recipient. The crypto world is no different.
You avoid this by using secure and private methods of communication. Even after you have set up your crypto wallets, the way you message your co-signers matters. You don’t want your sensitive financial information to be leaked or intercepted.
The most commonly-used platforms are Slack, Signal, Telegram, and even WhatsApp. Status is also another private and secure crypto-centric messaging app.
Consider communicating sensitive information using apps with a disappearing messages function. That way, if someone either clones, or takes control of the phone of an authorized signatory, they won’t be able to scrape historical communications data, and they won’t be able to impersonate you easily.
Regarding the importance of security and privacy in messaging, Status founder Carl Bennetts explains: "Secure messaging and encryption is becoming increasingly important amidst countless data breaches, deplatforming, and censorship of all kinds – with Status we strive to promote the sovereignty of individuals and uphold their rights."
The right messaging app can improve the security of your communications. But it’s ultimately up to you to implement and adhere to best practices to ensure data security.
Ensure no one keeps digital records of secret codes, private keys, and passwords online. Studies have shown that centralized exchanges are hacked because someone gained access to their online password manager. Also, avoid sending such confidential information online, no matter the messaging app.
Basic data hygiene practices such as not connecting to public WiFi hotspots, or using a VPN are also crucial.
Ready to Supercharge Your Crypto Accounting?
Stop wasting time, manually creating journal entries. Automate your accounting now, and enjoy error-free reporting
Learn how to scale your company's crypto & fiat financial operations
Your financial complexities are our specialties. Schedule your free consultation today and discover how Request Finance can transform your financial operations
Simplify crypto and fiat financial operations today
Rely on a secure, hassle-free process to manage your crypto invoices, expenses, payroll & accounting.
3. Use Transaction Monitoring Tools
When it’s that dreadful time of the year (tax season), transaction monitoring tools will be your best friend.
For crypto transactions, you will need to obtain proof of payment from a blockchain explorer, which allows you to browse through blockchain data and find past transactions. Depending on which blockchain networks you transact with, you may need to use a blockchain explorer for that specific blockchain network.
More often than not, you will find yourself having to use an Ethereum blockchain explorer, particularly given the popularity of Ethereum-based applications.
To find out which Ethereum blockchain explorers were most commonly used by the industry, we polled CFOs among our Request Invoicing’s corporate users.
Etherscan comes out on top, which is no surprise as its token check tool and balance check tool are incredibly convenient for accounting purposes. It also has a user-friendly interface with many additional features.
As mentioned above, if you are transacting on other blockchain networks, you should also find blockchain explorers specific to those networks. For instance, Polygon Network users use PolygonScan to verify transaction data.
4. Crypto-Friendly Accounting Software
In addition to transaction monitoring tools, crypto-friendly accounting software is another must-have tool in your toolkit.
Suppose you’ve been actively managing the company’s treasury by staking the company’s crypto assets to earn higher yields in liquidity pools. The time will come where you will have to account for all those gas fees, trade fees, trades, and payments involved. This can be a bookkeeping nightmare.
Today, there are accounting software and bridges to this accounting software that can make book-keeping far less of a hassle.
Once again, we polled our community of corporate crypto users.

Quickbooks and Xero are the most popular options. Netsuite and SAP One are also solutions crypto accountants work with. For certain jurisdictions like in France or Switzerland software, more specialized platforms are preferred given the sheer complexity involved in accounting standards in those markets.
But there’s just one problem: these accounting software alone cannot provide exchange rates, currency revaluation, nor do they support any digital currencies at all. A crypto accounting app/bridge is needed.
Cryptio, Ledgible and Cleverkin are the most commonly used options among our community of over 600 corporate users. Both Ledgible and Cryptio enable syncs with Quickbooks and Xero, while Cleverkin is closer to a dedicated accounting team at your service.
Cleverkin co-founder Dana Lesova explains: “For crypto accounting, transaction processing and administration, Cleverkin is the accounting team dedicated to make life easy for crypto companies”.
5. Treasury management with crypto
Last but not least, part of the duties of a finance manager working with digital currency is treasury management.
Often, that’s the sole reason why companies decide to become crypto-friendly in the first place. Other projects managing a native token simply need to manage crypto assets by nature.
DeFi platforms offer hundreds of options for putting your company’s crypto assets to work. To keep it simple, the most robust apps for earning yield on your crypt assets are AAVE, Compound, and Block.fi. Generally speaking, yields are variable, and can range from 2% to 20% annually.
Once again, we polled our community of corporate crypto users on their preferred treasury management platforms.

Moreover, there’s more to treasury management besides putting your crypto to work in DeFi platforms. You also need to manage what crypto assets you hold in your treasury.
Having a treasury with stable coins (USDT, USDC, DAI, etc.) is a great way to hedge against the volatility of cryptocurrencies. And in times of prolonged market downturns, you’ll be grateful for these stable assets.
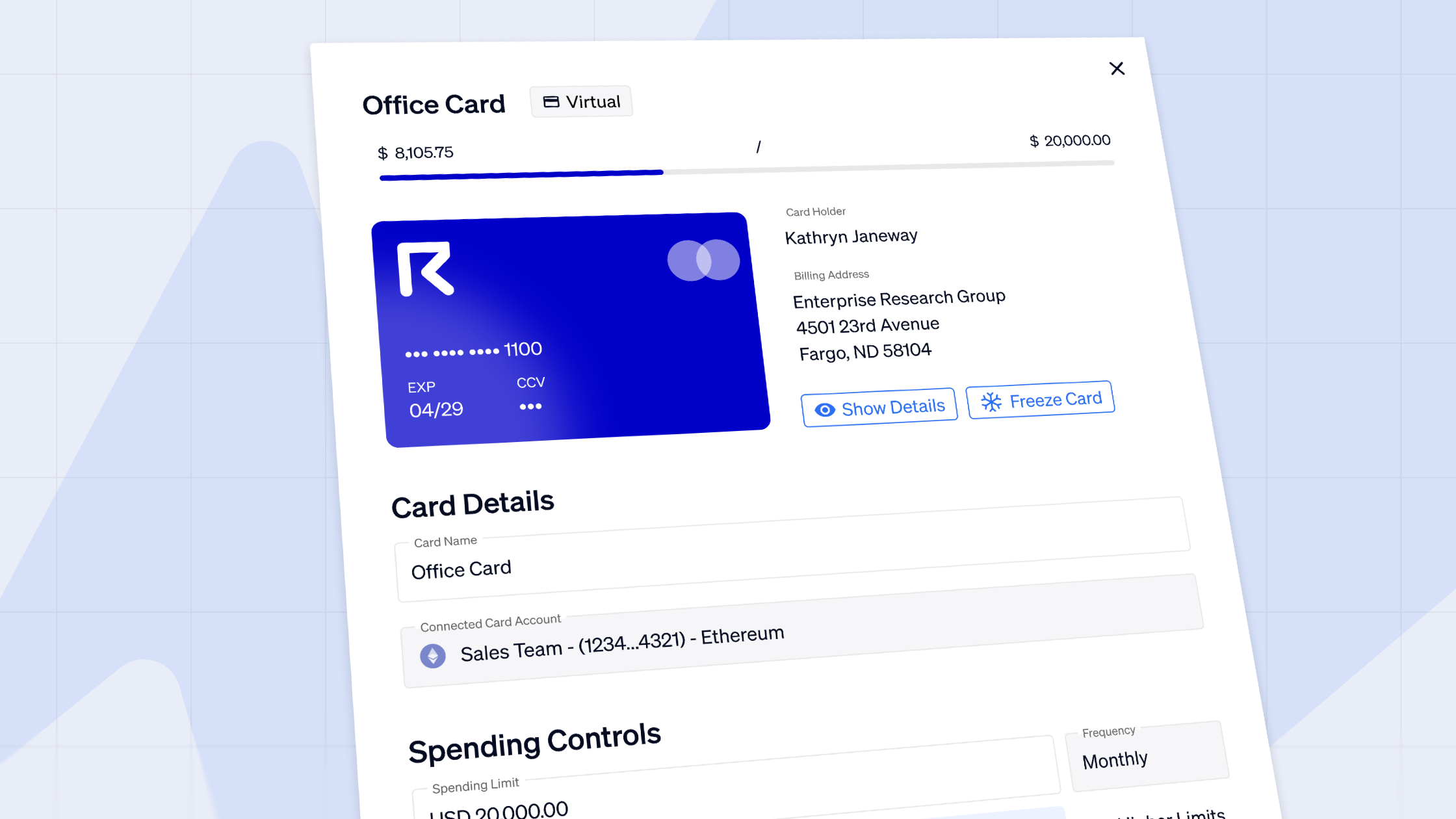
6. Streamlining payment processing on multiple blockchains
Request has become one of the most popular platforms for crypto companies to make and receive payments. To date the Request Invoicing app has processed over US$100 million in transactions. Today, more than 500 businesses are already using Request Invoicing.
Request’s Invoicing app allows users to easily generate or pay an invoice in over 24 different cryptocurrencies and stablecoins, and eight different fiat currencies. While the payment execution always takes place in a cryptocurrency, invoices can be automatically denominated in fiat currencies, such as USD, or EUR, with the use of Chainlink’s price feed oracles.
Invoicing with Request also provides a far easier, and less error-prone way to manage and account for crypto payments to multiple counterparties. The InvoiceMe feature allows companies to send pre-filled invoice templates containing the correct business information to their suppliers, helping companies reduce errors and save time. The integration with Gnosis Safe enables Request Invoicing users to make multiple payments in batches, even if they are denominated in different cryptocurrencies.
In addition to the core invoicing functions already available, Request Network plans to introduce more advanced features in the pipeline such as escrow, partial payments, and credit scoring. Request also has plans to introduce “smart invoices” which can be programmed, for instance, to automatically add a late payment fee to the amount due if the invoice has not been paid on time, eliminating the need to send another invoice to the counterparty.
7. Relocating
If you run a crypto company, consider relocating to Singapore. While relocation sounds extreme, companies intending to deal with crypto should seriously consider this option.
Over the last few years, hundreds of leading crypto companies have flocked to the crypto-friendly island state. For good reason too. For more than 10 years, the World Bank has ranked Singapore among the top 3 countries globally for its ease of doing business. More importantly, the central bank and tech industry regulators are crypto-friendly, and have some of the most progressive and clear laws governing crypto activities.
It is no coincidence that among those seeking economic haven in Singapore include high-profile industry figures like Vitalik Buterin, the founder of Ethereum, Binance’s billionaire founder Changpeng Zhao, and Jihan Wu, the billionaire co-founder of Chinese crypto mining tech group Bitmain.
Final thoughts
At Request, we believe that digital assets and cryptocurrencies will become a growing component of corporate finance.
We are constantly working towards developing compliance-ready tools and practices with leading companies in the crypto industry to better manage their crypto assets, and finance operations.
To understand more about how Request can help you, book an appointment with our team today for a free consultation.
Crypto finance tips straight to your inbox
We'll email you once a week with quality resources to help you manage crypto and fiat operations
Trending articles
Get up to date with the most read publications of the month.
Our latest articles
News, guides, tips and more content to help you handle your crypto finances.