How ByBit's Crypto Payroll Got Rugged of $4.3 million
How using spreadsheets cost ByBit $4.3 million in stolen payroll

Earlier this year, we highlighted the dangers of using spreadsheets to manage crypto payroll, analyzing the case study of how PeopleDAO was hacked for 76.5 ETH.
A High Court judgment from the global crypto hub, Singapore, revealed another unlikely victim. ByBit, one of the world’s largest crypto derivatives exchanges, had their crypto payroll exploited.
A woman identified as Ho Kai Xin was employed by WeChain Fintech, which was engaged to provide payroll services for ByBit.
In 2022, she stole $4.2 million worth of USDT, and over $100,000 in fiat, earmarked for ByBit’s payroll, then went on a spending spree.
With the stolen USDT, she splurged on - among other things - a $3.7 million freehold penthouse, $362,000 on a new car and $30,000 on luxury leather goods from Louis Vuitton.

Ready to Supercharge Your Crypto Accounting?
Stop wasting time, manually creating journal entries. Automate your accounting now, and enjoy error-free reporting
Learn how to scale your company's crypto & fiat financial operations
Your financial complexities are our specialties. Schedule your free consultation today and discover how Request Finance can transform your financial operations
Simplify crypto and fiat financial operations today
Rely on a secure, hassle-free process to manage your crypto invoices, expenses, payroll & accounting.
Why ByBit Got Rugged
Just like in the case of the PeopleDAO payroll hack, ByBit was using spreadsheets to manage their payroll operations.
Managing crypto payroll via spreadsheets is a ticking time bomb for crypto treasury managers, and Web3 CFOs, waiting to be exploited.
Anyone controlling the spreadsheet can easily inject their wallet address as a beneficiary, or swap out a rightful recipient’s address with their own.
Worse, this injection of malicious data into a spreadsheet is nearly impossible to spot. Crypto wallet addresses are long hexadecimal strings that are unreadable in natural language.
In fact, that’s exactly what happened with ByBit.
But instead of an external hacker - it was a rogue employee.
What happened
Ms Ho maintained two sets of Microsoft Excel spreadsheets. Each tracked the cash and cryptocurrency payments due to ByBit’s employees each month.
The spreadsheets listed the wallet addresses of ByBit’s employees where they were supposed to receive their paychecks.
ByBit’s employees could, and did regularly change their designated wallet addresses by communicating a new address to Ms Ho, who would then update the Excel files.
Ms Ho was the only person who updated the spreadsheets that listed the addresses designated by ByBit’s employees to receive their pay in cryptocurrency. These Excel files would be submitted to her direct superior, Ms Casandra Teo, for approval each month.

According to Court documents, she manipulated the spreadsheet files and wrongfully caused it to pay a total of 4.2 million USDT into the four crypto wallet addresses she controlled.
This happened over eight payments made between May and August, 2022, and was only discovered in September that year.
When confronted with the investigation findings, Ms Ho told ByBit that the wallet addresses belonged to her cousin. After this meeting, she ceased all contact with ByBit and WeChain.
ByBit then discovered that she went on to make several big-ticket purchases from July 2022 onwards, including the penthouse apartment with her husband, a new car, and luxury leather goods from Louis Vuitton.
She claimed that the penthouse was bought with money she earned from cryptocurrency trading “on MetaMask and Crypto.com”, despite claiming to have lost access to those accounts.
ByBit filed a lawsuit against her on Oct 12, 2022, and obtained injunctions to freeze the various assets. Ms Ho did not attend any court hearings or file submissions.
On March 30, 2023, ByBit applied for summary judgment, asking the court to decide in its favor without going through a trial.
Predictably, the Singapore High Court ruled in ByBit’s favor, ordering Ms Ho to return the stolen monies. But it is unclear how much of the stolen payroll funds will eventually be recovered.
How to securely automate crypto payroll
Processing payments like crypto payroll using spreadsheets creates an attack vector that allows malicious actors to inject themselves as beneficiaries.
But with the right tools like Request Finance, DAO treasury managers and Web3 CFOs can securely automate their crypto payroll processing.
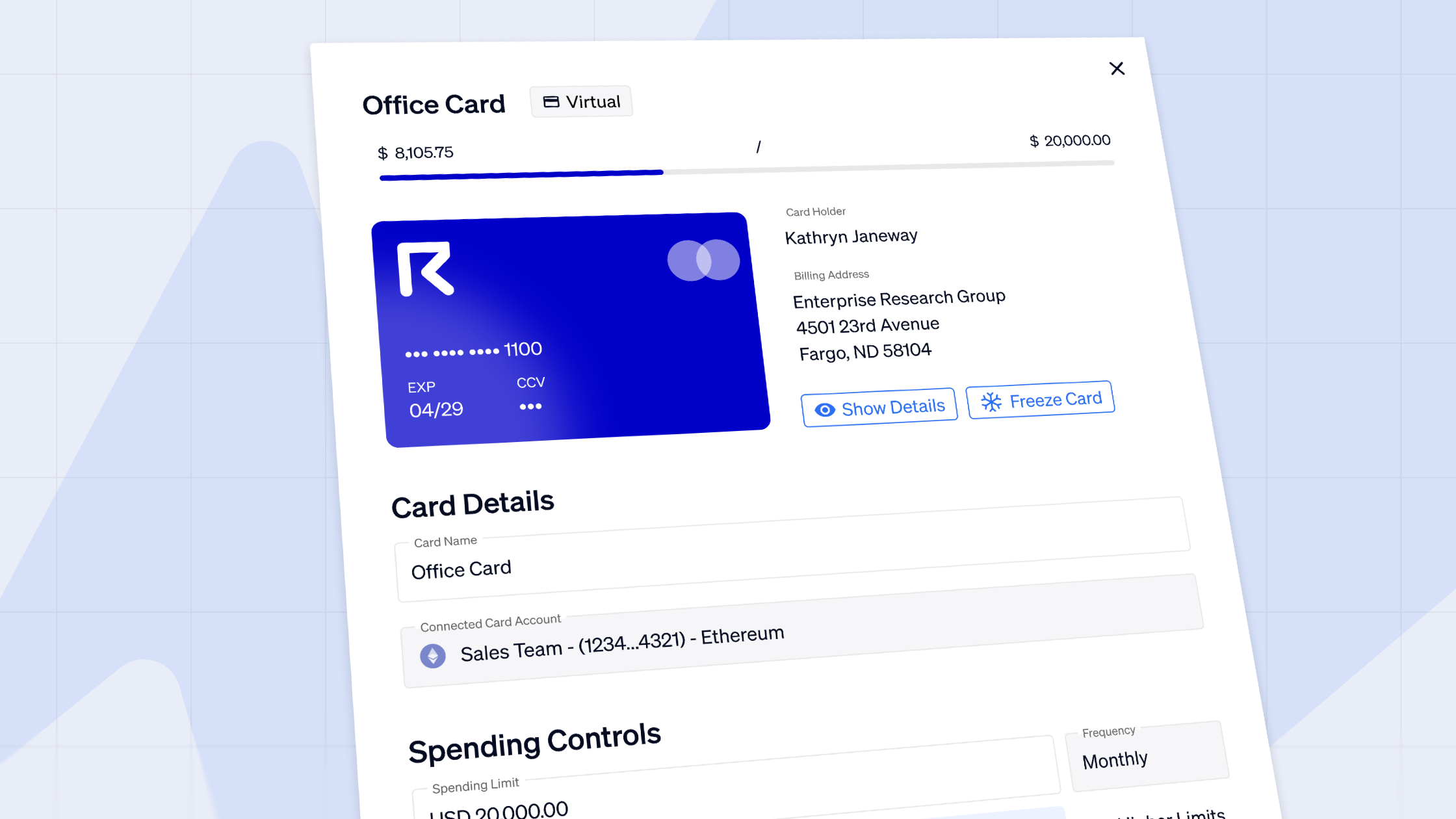
For starters, in Request Finance’s crypto payroll app, all employees’ billing information like names, roles, and wallet addresses are uploaded by an admin manager - or better still, by employees themselves.
Roles and permissions set in the app mean that this cannot be changed by other team members, or external parties whose roles do not grant them edit access.
It also allows for checks and balances within the members of the finance team.

Additionally, beneficiaries wallet addresses are stored in a contact database, and correlated to names, and email addresses.
This makes it easy to identify the owners of the wallet address by their names and email addresses.
Swapping out wallet addresses in an Excel sheet cannot happen here.

Also in the app, finance and operations teams must review and click the “approve” button for each payout - a crypto payroll, expense, or invoice. Only “approved” payment requests can be paid.
This enforces the practice of having teams to review each payout - in a human readable format that is easy to review.

All approved payout claims are displayed in a human readable format. This makes it easy to review who the beneficiaries are by their names and emails, prior to being sent to a wallet for signing.

These are just some features in Request Finance that are designed to prevent such attacks that can compromise Web3 companies, and DAOs crypto payroll processes.
Concluding thoughts
When people talk about security in decentralized finance (DeFi), the spotlight is typically on more sophisticated attack vectors. These include smart contract vulnerabilities, corrupted oracles, bridges, or blockchain network security.
But sometimes the simplest attack vectors can also be equally devastating.
The ByBit exploit highlights how the common practice of using Excel spreadsheets, or Google Sheets to manage crypto payroll is a critical vulnerability for DAOs, and companies that pay their employees, contractors, and contributors in crypto.

However, with tools like Request Finance, DAO treasury managers, and Web3 CFOs can automate their crypto payroll processes without sacrificing good governance and data security.
Crypto finance tips straight to your inbox
We'll email you once a week with quality resources to help you manage crypto and fiat operations
Trending articles
Get up to date with the most read publications of the month.
Our latest articles
News, guides, tips and more content to help you handle your crypto finances.